
Try it Now!
Leverage RDI to help transform your program to anticipate and counteract ransomware threats effectively.
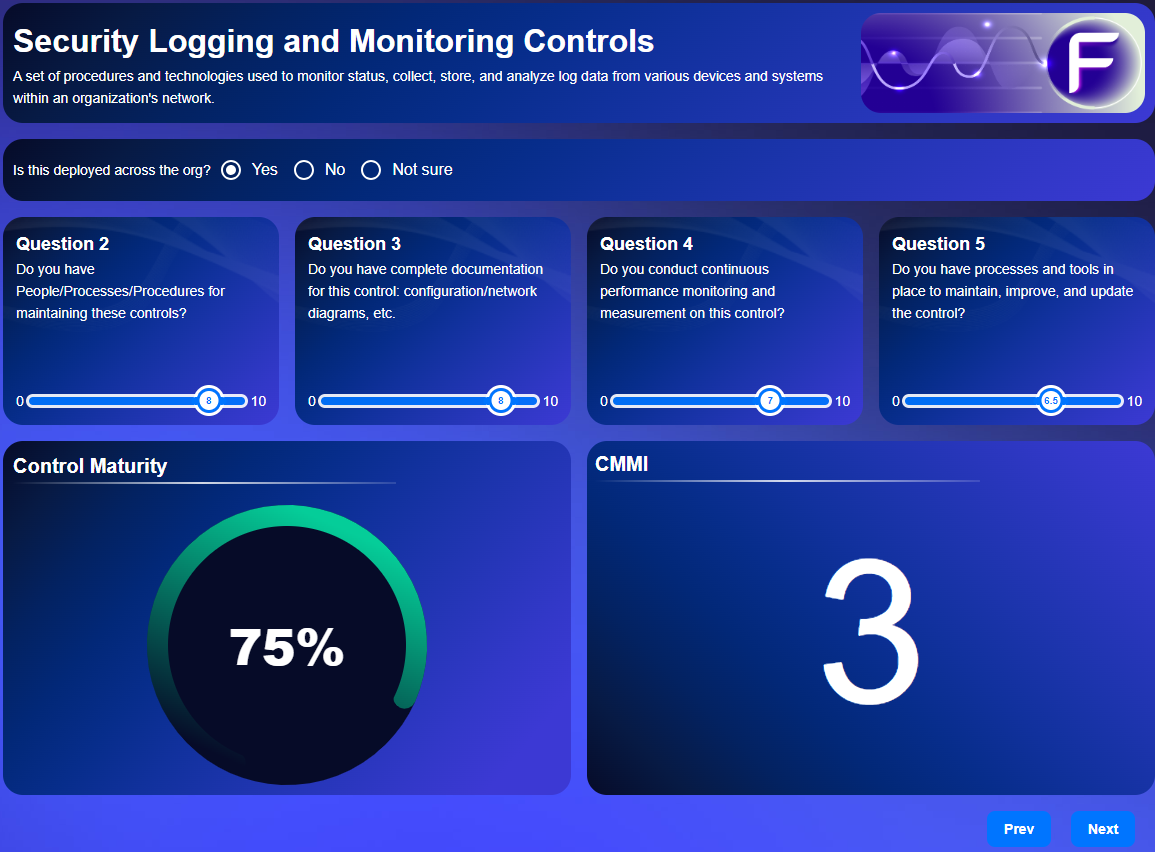
Answer 5 questions per control
Get real-time maturity result mapped to CMMI Levels 1-4
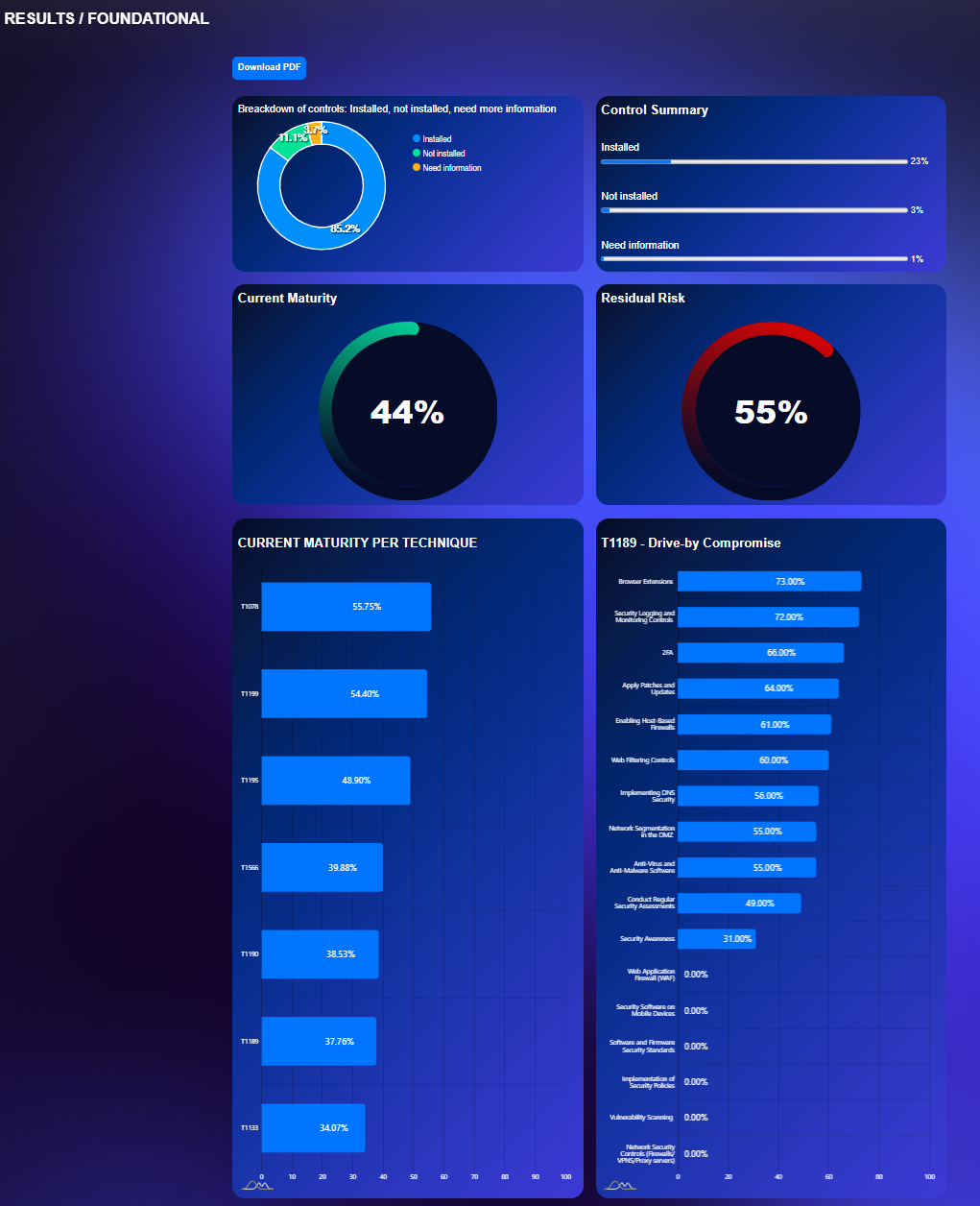
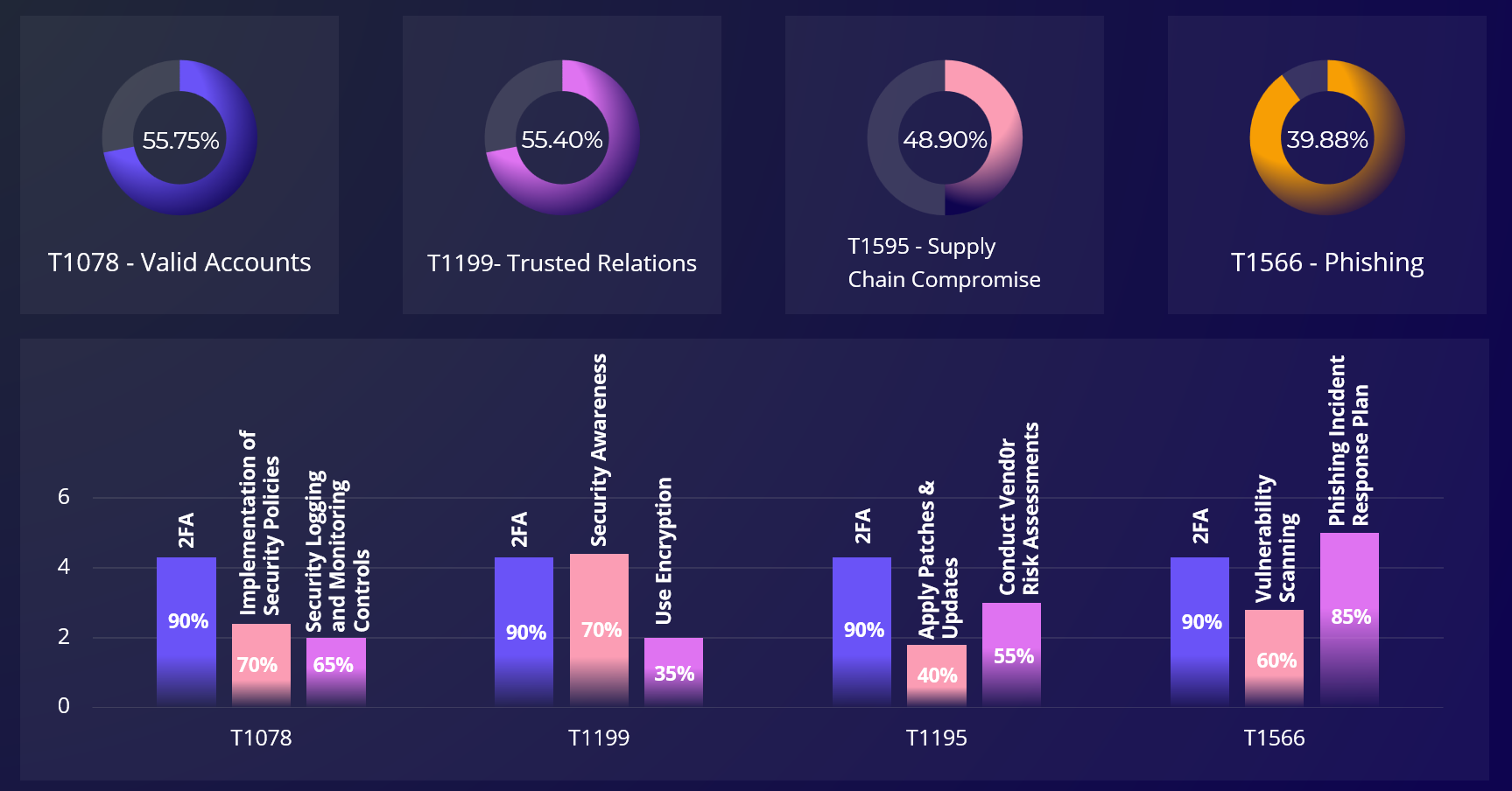
Create a Report of your readiness against well known MITRE ATT&CK Techniques
Use findings to define your strategy for proactive approach

Our Core Features


Complete Foundational Controls Assessment:
Dive into the core security controls you need.
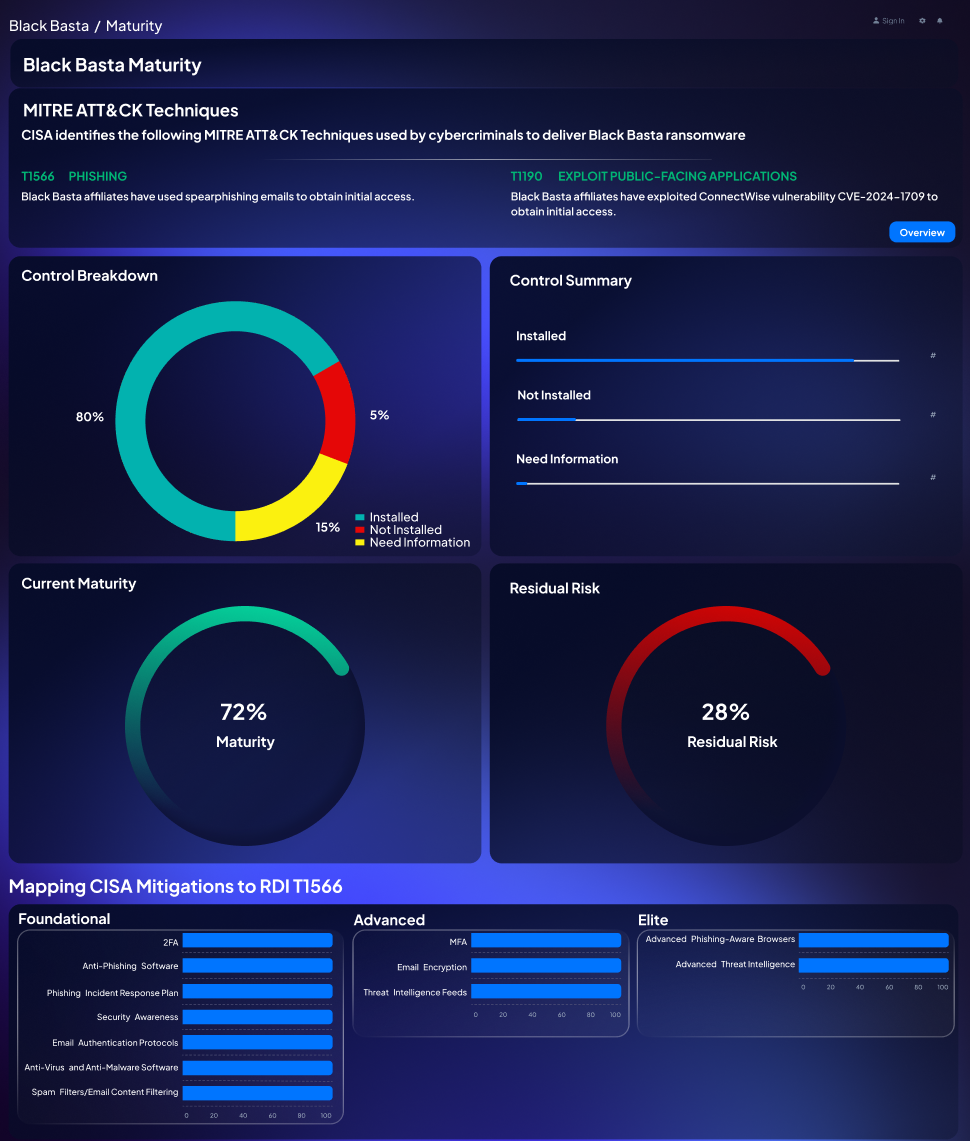
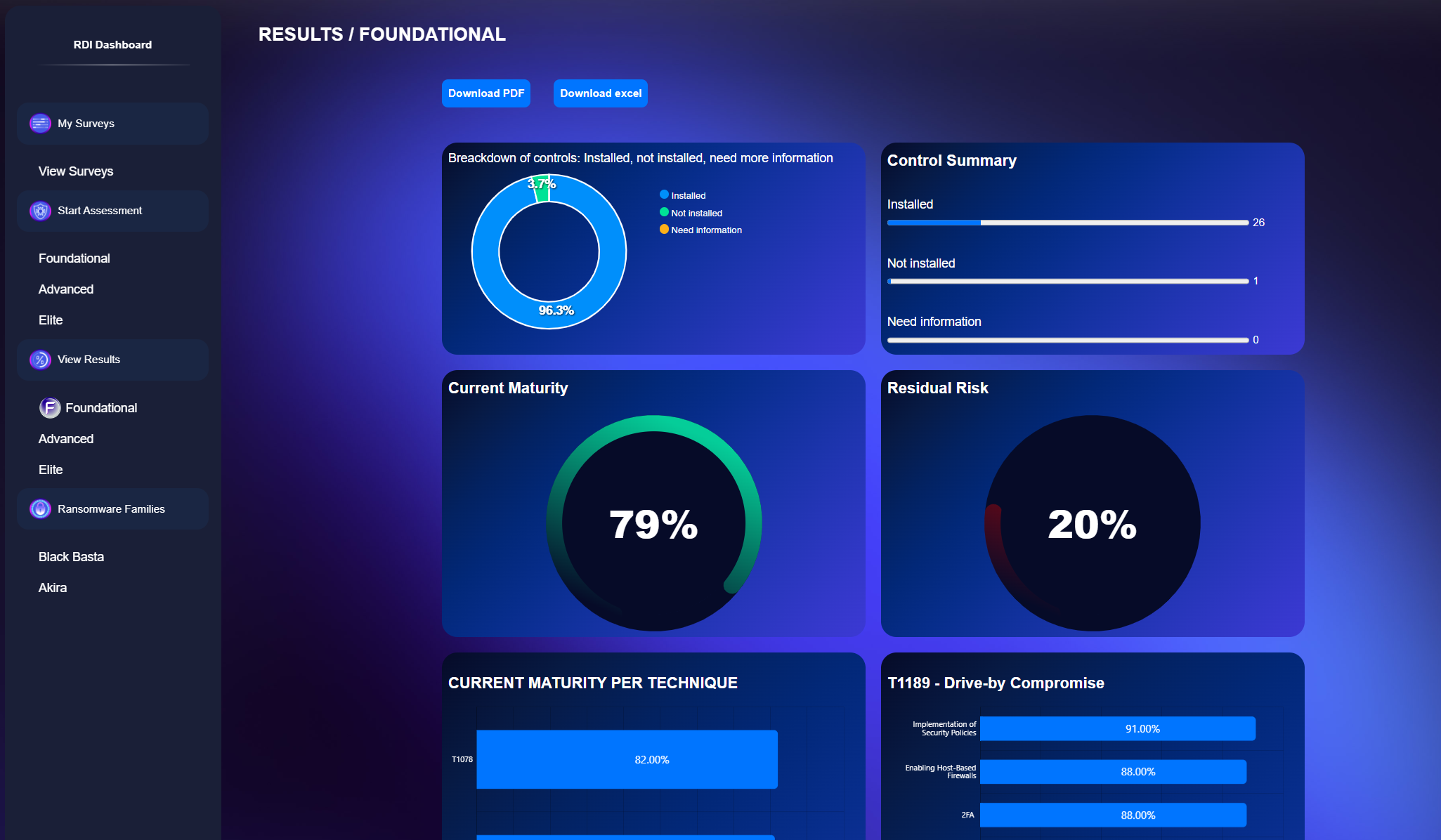
Maturity Dashboard:
Visualize your control deployment status and maturity across MITRE ATT&CK families.
Reporting:
Generate PDF reports.
Support:
Email support, with responses typically within 24 to 48 hours.
Complete assessment of Foundational, Advanced, and Elite Controls: Explore and engage with all essential security controls across every level.
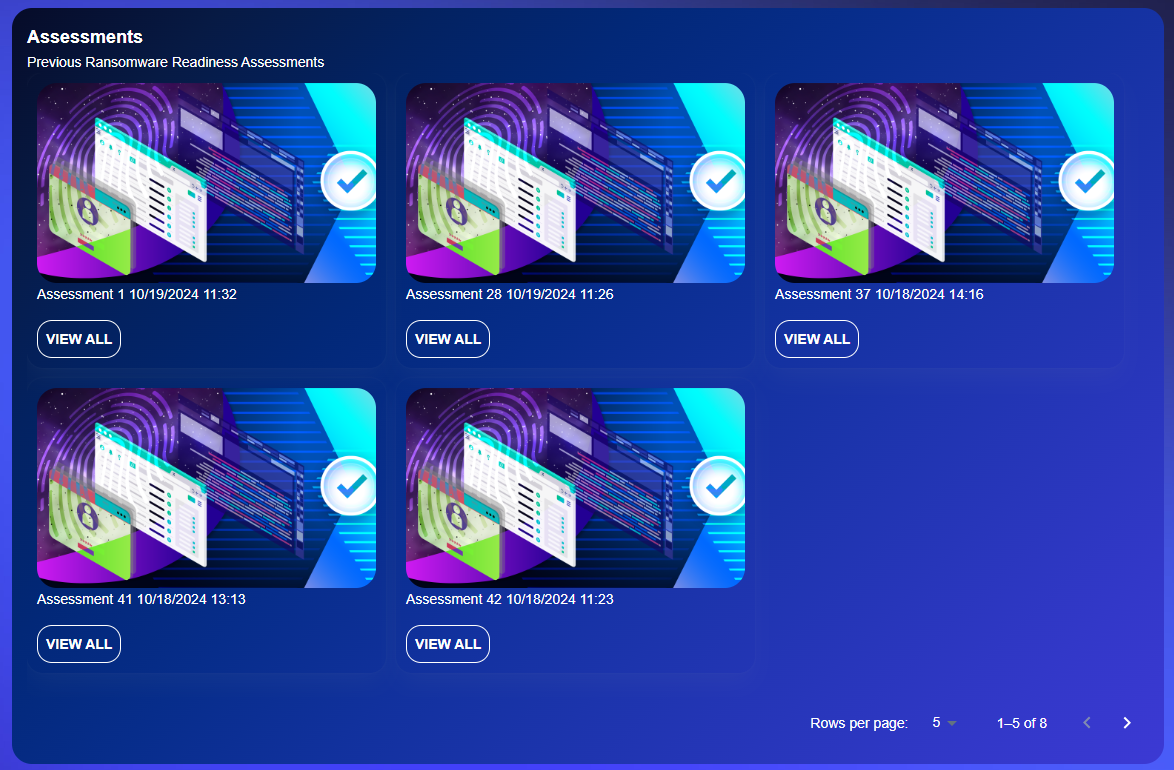
Admin Dashboard:
Keep track of your last 3 assessments for easy progress comparison.
Maturity Dashboard:
Visualize your control deployment status and maturity across MITRE ATT&CK families.
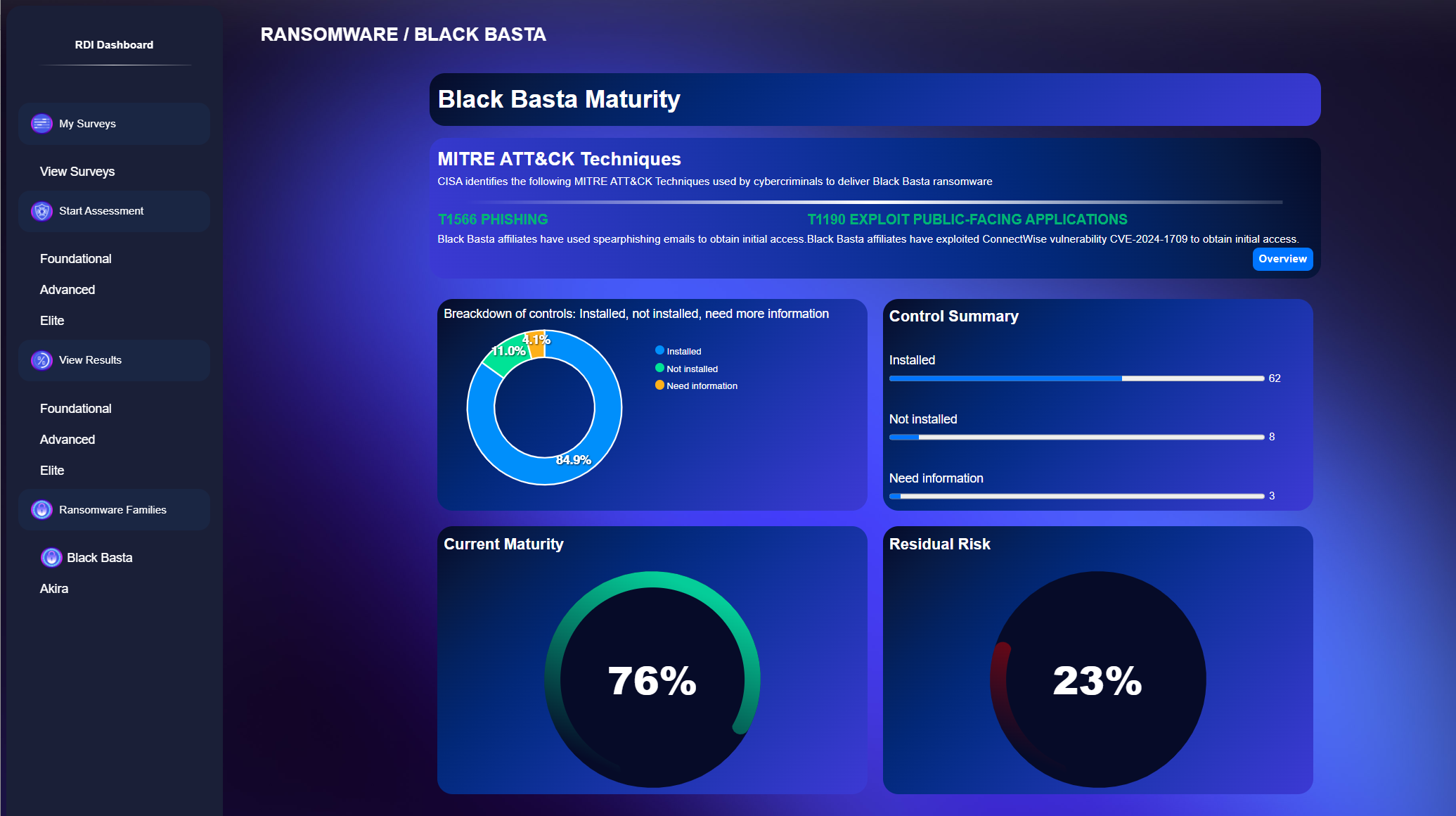
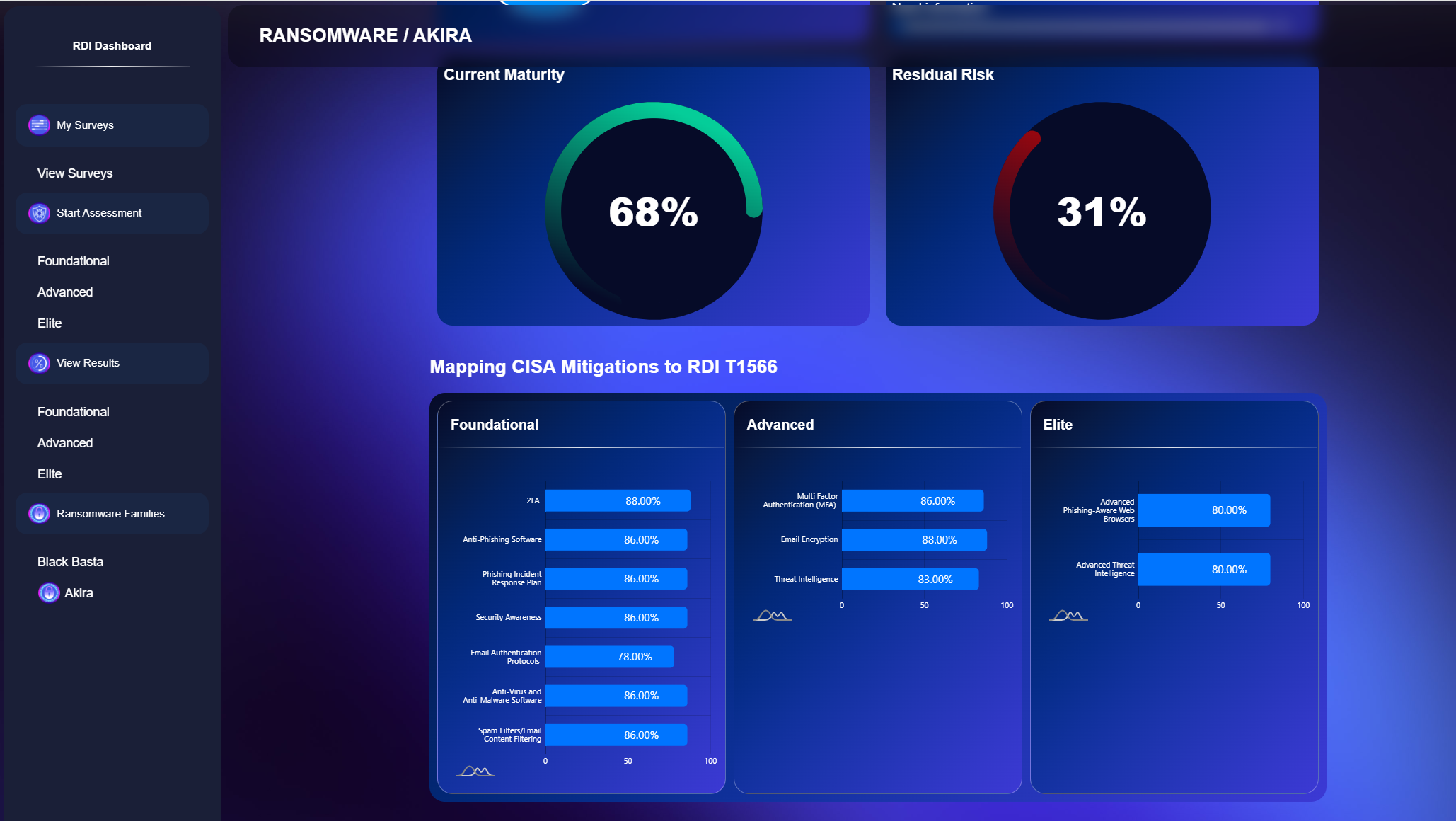
Ransomware Family-Specific Reports:
Receive detailed reports tailored to specific ransomware families.
Reporting:
Generate PDF or Excel reports.
Support:
Email support, with responses typically within 8 to 12 hours.